Honeypot Attempted Passwords

I’ve been running a honeypot for a while just to see what creepy things crawl around on the internet. One of the things I wanted to see is what credentials are probed when trying to sign in, so I equipped the honeypot with a fake WordPress login page.
Today, I’m writing about these credentials. For my evaluation I’m looking at data only from the past 6 months, more or less. On average, almost 80 attempts to login are made every day. Needless to say that for the honeypot, all attempts to login fail - there’s really nothing to login to.
Usernames
The WordPress login page does ask for a username too. Accordingly, my honeypot captures the values tried for usernames too. And without further ado, here’s the short list of user names that were actually tried.
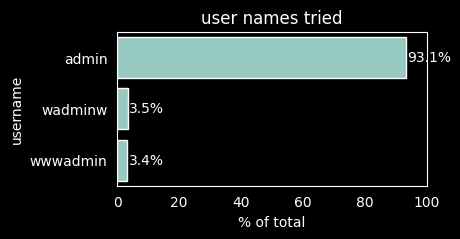
People and tools/bots trying to log in are not very creative in terms of usernames.
But then again, as long as people keep using usernames like admin, why would
anybody need to be creative? So, changing the default username to something less
obvious is probably a good idea.
Passwords
When it comes to passwords, the situation looks a little different. I’ve found
more than 1000 different passwords were tried. The most obvious one though,
admin, was tried by far the most often. What I could also observe is that some
tools/bots try to be clever and use the domain name of the page to construct a
password too. I’ve processed the data accordingly. Let’s say the page is hosted
on a domain called foobar.com, then in the chart below, the term <domain>
would reflect foobar. The term <tld> is used to refer to the top-level-domain,
i.e. for the above example that would be com.
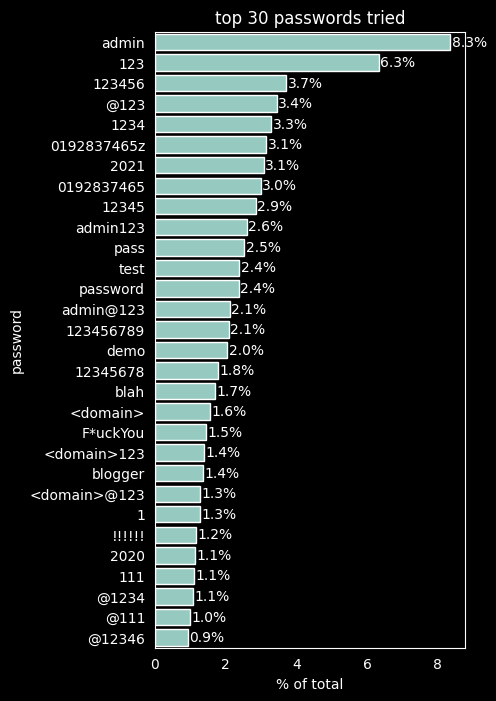
You can download the full list of unique passwords tried here (~9kB) .
Summary
Do yourself a favor: change default passwords, use secure passwords, or pass phrases.